Crypto.com Hacked: $30 Million Stolen using Tornado Cash

At the beginning of last week (mid-January 2022), the famous exchange Crypto.com suffered a hacking attack by malicious individuals who managed to compromise a number of accounts to the tune of USD 30 million. It all started when, on January 17, 2022, Crypto.com itself had reported that a small number of accounts had registered unauthorized cryptocurrency withdrawals. In response, the exchange immediately blocked withdrawals for the next 17 hours in order to prevent further suspicious actions.
Hackers Attack on Crypto.com: the numbers
Shortly afterwards came the official statement from the company with the damage count: 483 compromised accounts and about $30 million stolen (at the current exchange rate on January 25, 2022) distributed in 4836.26 Ethereum, 443.93 Bitcoin and about 66200 dollars in minor altcoins.
Tornado Cash
The hacker managed to escape with the loot and "clean up" about half of the sum, thanks to a decentralized application called Tornado Cash. But what is meant by "cleaning up" a certain amount of cryptocurrency? Let's take a little step back... Let's remember that Blockchain technology itself does not allow for maximum privacy in transactions. In fact, every deposit or withdrawal made in crypto, is recorded and stored in a Blockchain. This "database", even if it is decentralized, foresees the possibility to verify, for each movement of digital currency, two very important data: the withdrawal address and the deposit address. 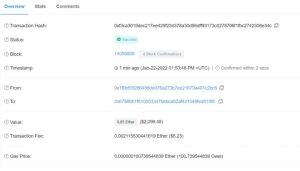 The image shows an example of a randomly selected transaction on etherscan.io. In this transaction, we can easily identify the two addresses in question, identified by the entries "from" and "to". By clicking on one of the two addresses, we can check some data such as the amount of tokens held and previous transactions made through that address. In case of exchange thefts or serious hacks, the stolen funds are usually monitored by the offending community. What is the purpose of all this if the addresses remain pseudo-anonymous? Simple, for the purpose of blocking the use of such funds. In some cases, cryptocurrency issuers such as "Tether Treasury" or some centralized exchanges can "freeze" these funds to make them unusable by those responsible for the theft.
The image shows an example of a randomly selected transaction on etherscan.io. In this transaction, we can easily identify the two addresses in question, identified by the entries "from" and "to". By clicking on one of the two addresses, we can check some data such as the amount of tokens held and previous transactions made through that address. In case of exchange thefts or serious hacks, the stolen funds are usually monitored by the offending community. What is the purpose of all this if the addresses remain pseudo-anonymous? Simple, for the purpose of blocking the use of such funds. In some cases, cryptocurrency issuers such as "Tether Treasury" or some centralized exchanges can "freeze" these funds to make them unusable by those responsible for the theft.
How Tornado Cash works
It is at this point that Tornado Cash comes into play. The decentralized application serves to guarantee maximum anonymity on the part of those who use the protocol, in order to "clean up" the funds transferred via Tornado Cash, thus preventing the identification of the addresses responsible for the fraudulent transfer. Specifically, Tornado Cash allows to deposit, within the protocol, a defined amount of tokens and withdraw the same tokens in a completely anonymous way, without allowing the most curious to trace the history of suspicious transactions. Until now, it is the most widely used decentralized protocol to maintain on-chain privacy and break the connection between deposit and withdrawal accounts. 
Hacker Attack: Crypto.com's Response
Crypto.com, in spite of the damage, immediately reassured the entire community that their funds were safe and that customers who had been robbed would be reimbursed through the company's guarantee fund. Crypto.comCEO Kris Marszalek, the day after the theft, reassured that his company had already taken action by whitelisting the new addresses. Moreover, Crypto.com has introduced a new security measure that allows a withdrawal to be made only after 24 hours of adding a new address to the whitelist. Our thought on the matter Clearly, we sincerely hope that certain events will no longer occur in the future and that more efficient security measures will be introduced into centralized exchanges, such as Crypto.com. At the same time, we do not condemn a decentralized protocol such as Tornado Cash, labeling it as a mere tool useful for "laundering" cryptocurrencies derived from illegal activities, since the application, by its nature, aims at maintaining the privacy of users, a factor, that of the protection of user privacy, of absolute centrality for the supporters of decentralization. Having said that, we also want to emphasize how true is, in our opinion, the saying: "not your keys, not your money": that is, if you are not the keeper of the keys of your deposit, you are not really the owner of your money! We invite all the community to take a cue from similar events to reflect on the undeniable fact that to be really in possession of their funds, you must necessarily use decentralized wallets, obviously taking care to choose those with high security standards, such as Phantom or MetaMask. However, the right to be in real possession of our cryptocurrencies, also involves some duties, first of all to be properly informed about what are the benefits and risks of making actions in the decentralized world.